Point to Point Virtual Prive Networks and Remote Access, RAS
A Point-to-Point Virtual Private Network (VPN) is a type of VPN connection that establishes a secure, encrypted connection between two devices, typically a remote computer and a corporate network. In a Point-to-Point VPN, data is transmitted between the two devices over a secure tunnel, which is encrypted to protect against unauthorized access and interception. This type of VPN connection is commonly used in situations where a remote worker needs to securely access corporate resources or data over the internet.
One of the main advantages of a Point-to-Point VPN is its flexibility. It can be set up quickly and easily between two devices, regardless of their location, making it an ideal solution for remote workers or employees who need to access company resources while traveling. Another benefit of a Point-to-Point VPN is that it can provide a high level of security, ensuring that sensitive data is kept confidential and protected from unauthorized access. This is achieved by using advanced encryption techniques and authentication protocols to establish a secure connection.
However, one potential disadvantage of a Point-to-Point VPN is that it can be more difficult to manage and scale than other types of VPNs. This is because each connection must be configured individually, which can be time-consuming and complex in larger environments. In summary, Point-to-Point VPNs are a useful tool for establishing secure, encrypted connections between two devices, typically a remote computer and a corporate network. They provide flexibility and high levels of security, but may require more management and configuration than other types of VPNs.
One of the main advantages of a Point-to-Point VPN is its flexibility. It can be set up quickly and easily between two devices, regardless of their location, making it an ideal solution for remote workers or employees who need to access company resources while traveling. Another benefit of a Point-to-Point VPN is that it can provide a high level of security, ensuring that sensitive data is kept confidential and protected from unauthorized access. This is achieved by using advanced encryption techniques and authentication protocols to establish a secure connection.
However, one potential disadvantage of a Point-to-Point VPN is that it can be more difficult to manage and scale than other types of VPNs. This is because each connection must be configured individually, which can be time-consuming and complex in larger environments. In summary, Point-to-Point VPNs are a useful tool for establishing secure, encrypted connections between two devices, typically a remote computer and a corporate network. They provide flexibility and high levels of security, but may require more management and configuration than other types of VPNs.
One of the most ever-present and ancient uses of the Internet and networking has been to provide remote access to networks or network resources. Since the early 1980's, different remote access protocols have existed to allow users to remotely dial in to a network of choice; while some of these protocols have come and gone, many of them remain widely in use even today in dial-up WAN access and business VPN networks.
Question: How does the internet provide remote access to networks or network resources?
The internet provides remote access to networks or network resources through a variety of protocols and technologies. Some common methods of remote access include:
Overall, the internet enables remote access by providing secure and encrypted connections between remote users and network resources, allowing users to work from anywhere with an internet connection.
Question: How does the internet provide remote access to networks or network resources?
The internet provides remote access to networks or network resources through a variety of protocols and technologies. Some common methods of remote access include:
- Virtual Private Network (VPN): A VPN creates a secure and encrypted connection between a remote user and a private network. The user can then access resources on the network as if they were physically present on the network.
- Remote Desktop Protocol (RDP): RDP allows a user to remotely access and control a computer or server on a network. This allows the user to access files and applications that are only available on that specific machine.
- Secure Shell (SSH): SSH is a protocol used to remotely access and manage network devices and servers. It provides secure communication between the user's computer and the remote device.
- Remote Access Services (RAS): RAS allows remote users to dial into a network and access resources over a secure connection. This method is commonly used by businesses to allow employees to work remotely.
- Web-based access: Many networks provide web-based access to resources such as email, file sharing, and databases. This allows users to access these resources from any device with an internet connection.
Overall, the internet enables remote access by providing secure and encrypted connections between remote users and network resources, allowing users to work from anywhere with an internet connection.
RAS
RAS, or Remote Access Service, is a rarely-used, unsecure, and outdated Microsoft offering in the area of remote access technology. You should know for the exam that RAS provides dial-up access and once was the protocol of choice for connecting to the Internet.
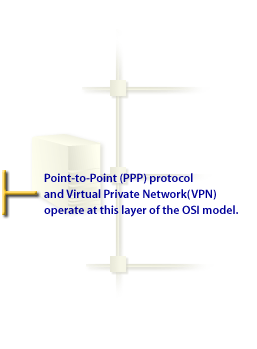
PPP
RAS was eventually replaced by PPP, the most common dial-up networking protocol today. PPP, or point-to-point protocol, utilizes a direct connection from a client to WAN over TCP/IP.
This is advantageous for dial-up networking services as most people today wish to be able to use the Internet, which of course requires TCP/IP networking. When you think dial-up access, think PPP.